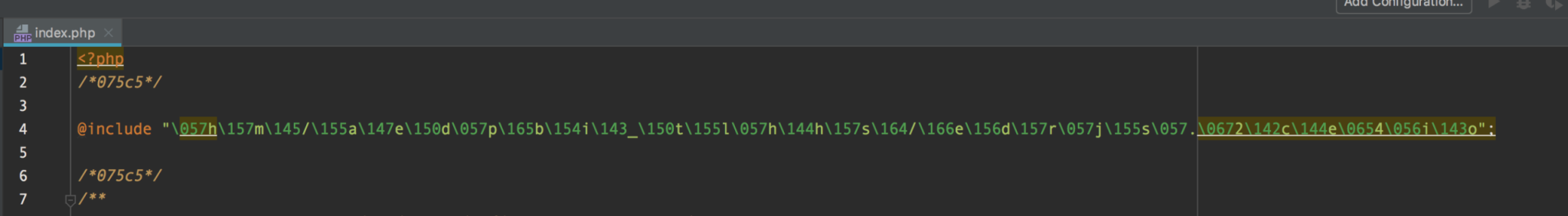
You may not always need professional services to remove WordPress malware. It's always a huge problem when a WordPress website gets hacked and loaded with a ton of malware and you may not have a budget to pay for WordPress malware removal services. Not only can it affect your SEO, but the malware will also tear your website apart with what looks to be unlimited pop-ups. I've seen times when malware will cause computer viruses to be downloaded to the computer of any visitor that goes to your website. This could be a reason why Google will penalize your website when its crawlers detect malware. Here are a few reasons that can cause WordPress malware within your website. Your hosting can play a major factor as well. If your hosting provider is not keeping your hosting packages such as PHP up to date, your site will be vulnerable. For this reason, we advise ensuring your web host is keeping your host packages up to date. WordPress much like many other platforms is prone to hacks but what makes WordPress more vulnerable is the fact that it's extremely popular and plugins are not vetted for security or best practices. Plugins and the WordPress development team release updates for a few reasons. They’ll send an update for additional features that have been added, bug fixes to current features, or more importantly security vulnerability fixes. If your WordPress installation is not being constantly updated, every update missed increases your risk of getting hacked. You would be surprised that many of the symptoms are not apparent. A lot of the time, you may not even know your site has malware until something breaks. Maybe a page doesn't load properly or has a blank page. You may even start seeing weird PHP errors. If you're running the WooCommerce plugin, you may get complaints from your customers about credit card fraud. The more visible symptom is Elements showing on your website that you did not create, or tons of pop ups. The symptoms all depend on the type of malware and the intentions of the creator which can range from advertising by blasting every page with 100 pop-ups or credit card fraud. Before one can fix a malware hack, one has to understand how it works. The fix will not work for everybody but it is definitely worth a try given the circumstances. The reason why this may not work for everybody is that some malware has a way of duplicating itself and returning. Essential, the malware developer will create one file. This file we can call the "Master File". This master file is responsible for checking if the malware code snippet is still present in your file system. If you've ever wondered why malware keeps returning, this is why. The malware developer will cleverly attach this file to either a PHP script that runs on a cron job or a PHP script that is used on typical tasks. For instance, every time a user creates a new post, the PHP script to create a new post would trigger the execution of that "Master File". Finding this master file is extremely tricky, the majority of the time we have to download the full file system to a local WordPress development environment and trace back from the modified WordPress core scripts that have the malware included. This method is very time consuming and daunting so if this is the route you need to go, warm up a pot of coffee and get your favorite chair back massager because you will be there for a while. There's a little twist to complex malware. A lot of the times, malware is designed to be untraceable. The best way to trace it back to the master file is to search through the file system and seek out the function that is in the malware code. Example: in the image below of a malware code snippet we can see that the "@include" function is used. We also see that whatever is creating this snippet, is commenting the code with "/*075c5*/". These 2 pieces of text are what I would use to search within the file system for the suspect, the "Master File". Once the master file has been found, you can proceed to remove the code snippets out of the file system without having to worry about them returning. We consider simple malware as one that does not have a master file as mentioned above. To fix simple malware it's as easy as removing the snippet similar to the above image. To make things that much easier to manage and to add a bit of malware & security prevention. We recommend the plugin Wordfence. Wordfence will not only scan your system for modified WordPress core files but it allows you to scans for malware, and other security issues. You will also have the option to restore the core files and also delete malicious files. For a full featured list of the Wordfence capabilities you can read more on Wordfence.com With the increase of WordPress popularity, you can expect an increase in malicious developers creating malware. Keep the plugins in your website to a minimum, use security plugins like Wordfence, and stay on top of your hosting provider about keeping your hosting environment up to date. Introduction
Why does it happen?
Web hosting
Outdated Plugins
Outdated WordPress Platform
The Symptoms of malware
How do I remove wordpress malware?
Complex Malware
How is WordPress malware developed?
Tracing down the Malware: The Manual process
Simple Malware
WordPress plugin alternatives
Conclusion